Table of Contents
Government abstract
“Are you aware what a non-fungible token (NFT) is?” This query began a series response that resulted in an investigation by a various crew into how Statistics Canada (StatCan) may use blockchain, or distributed ledger know-how, to authenticate a doc. The query was posed as a part of a extra vital thought of how the Dissemination Division may use NFTs, or comparable know-how, to authenticate the merchandise leaving the StatCan web site. Initially, our crew was composed of inner StatCan staff: Mathieu Laporte, Director of the Dissemination Division; Jacqueline Luffman, Chief of Publishing Companies; and Lillian Klein, Analysis Librarian. These people mentioned the thought amongst different StatCan workers to guage whether or not it was possible. Nonetheless, as we acknowledged a niche in our blockchain expertise, we reached out to lecturers who analysis numerous elements of blockchain know-how. By way of these conferences, we had been related to 4 blockchain specialists: Dr. Florian Martin-Bariteau from the College of Ottawa, Dr. Jeremy Clark from Concordia College, Dr. Victoria Lemieux from the College of British Columbia and Dr. Tracey Lauriault from Carleton College. We met with these specialists for a brainstorming session, the place Jeremy Clark introduced the thought of utilizing digital signatures to authenticate StatCan paperwork. With this concept in thoughts, a crew of researchers was shaped to discover up-to-date cryptographic know-how and purposes to develop a complete understanding of the know-how and decide whether or not utilizing this know-how in StatCan’s work could be significant. Our analysis crew contains Kathryn Fedchun, a PhD pupil at Carleton College; Didem Demirag, a PhD candidate at Concordia College; and Lillian Klein, a analysis librarian with StatCan. This paper summarizes months of collaborative work accomplished by this crew.
The primary focus of this mission is to grasp extra about blockchain and see whether or not, as StatCan expands its web site, it may use blockchain know-how to allow customers to authenticate the information downloaded from the web site. With an elevated understanding of those rising applied sciences, the goal of this mission is to develop a means of authentication that may permit customers to confirm that the fabric downloaded from the StatCan web site has not been tampered with and was produced by StatCan. This is able to enhance total belief within the company as a statistical group. By utilizing blockchain to find out the authenticity of its information, StatCan has the capacity to extend social belief with its customers. It was recognized that the perfect methodology of authenticating the information needs to be simple to make use of and accessible in a web-based and offline format to make sure customers with various levels of Web connection can authenticate their information.
Our analysis efficiently outlined and defined what blockchain is and recognized how blockchain is at present being utilized in a Canadian context. We discovered that there has not too long ago been a name to motion for presidency companies to embrace blockchain know-how and take strides to implement it of their work. To create a well-rounded evaluation of the know-how, we included a evaluate of issues concerning blockchain. We centered totally on the environmental affect, the public notion of the know-how and any potential backlash our crew may anticipate, the dearth of rules, and the potential to be blinded by the hype of blockchain know-how. Lastly, we accomplished a quick comparability of 5 blockchains that could possibly be utilized in our answer. This comparability focuses on common details about every chain, together with the transactions per second, the consensus mechanism, whether or not it’s non-public or public, and every blockchain’s environmental affect. This evaluation enabled us to determine that Avalanche is the most suitable choice for us as we transfer ahead with our technical answer.
With the information gained from this analysis, our crew recommends that this mission could possibly be the company’s alternative to reply the decision to motion. We suggest that StatCan conduct a pilot mission based mostly on Jeremy Clark’s thought about utilizing digital signatures and construct an utility that customers can obtain to authenticate their information. We suggest utilizing a hybrid mannequin with a blockchain that can permit each on-line and offline customers to authenticate their information. The technical particulars of this mission are defined in depth beneath; to summarize:
In the hybrid answer, authentication will happen via an utility that customers should obtain. The record of hashes of recordsdata is up to date periodically to comprise the hashes of recent StatCan merchandise. The authentication of a file will happen as follows: the consumer might want to add the file needing authentication to the app. This motion will immediate the app to compute the hash of the file and evaluate it with the record of already present hashes from StatCan merchandise. The app will then inform the consumer whether or not the file is legitimate.
This answer provides super worth to the company’s transparency and belief with customers. Internet hosting the hash values on the blockchain creates an immutable report over time of the merchandise the company has launched and will increase customers’ capacity to belief the info downloaded from the StatCan web site. This mission is a chance to experiment with blockchain know-how with out overhauling the company’s present system.
Introduction
Within the age of info, it’s essential to acknowledge the rising quantity of digital info accessible to Canadians and their rising mistrust of digital sources (Ipsos Public Affairs for Canada’s Centre for Worldwide Governance Innovation [CIGI-IPSOS], 2019). In accordance with Ipsos Public Affairs for Canada’s Centre for Worldwide Governance Innovation (2019), 36% of Canadians really feel that the federal government contributes to their sense of mistrust in the Web. As Statistics Canada (StatCan) is the department of presidency accountable for disseminating info to Canadians, it mustn’t ignore this statistic. Throughout the 2020/2021 fiscal yr, the StatCan web site had over 28 million net web page guests and 766,589 desk downloads (Statistics Canada, 2021). StatCan prides itself on its transparency and accountability to the general public and strives to fulfill the wants of its customers (Statistics Canada, 2018). As a corporation, StatCan advertises itself as being “a trusted supply of statistics on Canada” (Statistics Canada, 2018). In accordance with StatCan’s Belief Centre, “the individuals of Canada can belief that info gathered from them, and about them, is finished so for them—and that these actions are carried out with integrity and the best moral requirements” (Statistics Canada, 2018). The Statistics Act guides StatCan to make sure that it promotes and develops “built-in social and financial statistics pertaining to the entire of Canada” (Statistics Act, 1985).
Customers rely on the company and anticipate to entry and obtain genuine, dependable information after they enter the StatCan web site. However as soon as a product has been downloaded, it’s difficult to validate that it belongs to StatCan and has not been tampered with by a malicious actor. Which means that customers might imagine they’re accessing untampered information from StatCan when downloading a corrupted comma-separated worth (CSV) file. Concerning the probability of StatCan turning into a sufferer of cyber threats by the hands of malicious brokers, the elevated variety of ransomware assaults on Canadian organizations reveals that the nation is a possible goal (Communications Safety Institution Canada, 2021). Subsequently, as StatCan begins to plan the enlargement and innovation of its web site, it’s important that it think about the way it can provide customers the flexibility to confirm and authenticate the information they obtain from the web site.
This analysis goals to examine whether or not StatCan may reply to the authentication hole on its web site by integrating rising applied sciences into its present publication strategies. To discover solutions, we started by familiarizing ourselves with the present analysis surrounding blockchain and distributed ledger know-how. We then thought-about the significance of report retaining, confidentiality, belief and authentication. We checked out a number of examples of different Canadian organizations and authorities companies utilizing blockchain and located a number of articles calling on the federal government to undertake this new know-how. Nonetheless, we additionally thought-about issues associated to these rising applied sciences, together with environmental affect, public picture and potential backlash, a scarcity of regulation, and the opportunity of being blinded by the “hype.” We investigated 5 blockchains that could possibly be utilized in our system design: Ethereum, Avalanche, Cardano, Hyperledger and Solana. With a higher understanding of the know-how accessible to StatCan, we labored to conceptualize a system that permits customers to authenticate the information they obtain from the web site. Our aim is that the system permits customers to confirm that the materials downloaded from the web site has not been tampered with and was produced by StatCan. We imagine that our methodology of authenticating information ought to be accessible in on-line and offline codecs to make sure that customers with various levels of Web connection can authenticate the information. Our crew prioritized this element to serve all Canadian customers, realizing that high-speed Web connection is inconsistent due to the digital divide within the nation (Canada’s Public Coverage Discussion board, 2014). Moreover, we prioritized usability when contemplating choices for an answer, which must be so simple as doable to make sure the know-how is accessible and straightforward to grasp by customers.
Earlier than an answer will be really helpful, it’s essential to introduce the know-how behind it to offer the context required to grasp how the know-how can assist StatCan accomplish its aim. The primary options that should be understood are the digital signatures and hash features that assist our idea. Along with the introduction and literature evaluate, Appendix A has a glossary of phrases to assist readers perceive the extra technical materials.
Gaps within the literature
All through the analysis course of, we discovered a few gaps within the literature. Provided that blockchain remains to be a comparatively new know-how, particularly for presidency use, it’s not stunning that gaps had been discovered. It was tough to seek out any concrete Canadian authorities rules or insurance policies on easy methods to incorporate blockchain. Which means that directives on the implementation of blockchain inside the authorities are nonetheless coming to mild. This hole leaves our crew with questions surrounding how insurance policies may change sooner or later to simplify or complicate the implementation of this mission. One other recognized hole is the dearth of selection in the best way organizations have printed their methodology of incorporating blockchain into their day by day work. We discovered numerous materials about how blockchain is being utilized in cryptocurrency, report retaining and monetary know-how (fintech). Nonetheless, it was tough to decide how blockchain is utilized by organizations each day. We had been additionally unable to seek out vital info on the authorized implications of utilizing blockchain for our functions. For instance, within the case of well being information mentioned beneath, it was tough to find out how affected person recordsdata had been uploaded or tracked on the blockchain. Moreover, it was tough to seek out analysis on comparable initiatives. We had been unable to find printed analysis in search of to tackle the difficulty of easy methods to give customers the flexibility to authenticate information which have been downloaded from a web site. We imagine that our mission fills a few of the gaps within the literature and is a invaluable step within the path of recent know-how for StatCan.
Methodology
Systematic literature evaluate
We carried out a systematic literature evaluate for this examine, which allowed us to grasp “the breadth and depth of the prevailing physique of labor and determine gaps to discover” (Xiao and Watson, 2019, p. 93). A profitable systematic literature evaluate includes three phases: planning, conducting and reporting (Xiao and Watson, 2019, p. 102). The primary stage, planning, is when researchers “determine the necessity for a evaluate, specify analysis questions, and develop a evaluate protocol” (Xiao and Watson, 2019, p. 102). Within the second stage, researchers conduct the analysis and “determine and choose major research, extract, analyze, and synthesize information” (Xiao and Watson, 2019, p. 102). Lastly, the third stage includes researchers “writ[ing] the report back to disseminate their findings” (Xiao and Watson, 2019, p. 102). For this mission, we had the next three analysis questions in thoughts:
- What’s blockchain, and the way produce other authorities companies and organizations used this know-how?
- How can this know-how be used to extend report retaining, confidentiality, belief and authentication on the Statistics Canada web site?
- How can we use this new know-how in our answer to authenticate information?
Within the planning part of this examine, we compiled a listing of search phrases that centered on our areas of curiosity on this mission. The record of search phrases will be present in Appendix B. As Xiao and Watson (2019) described of their article on easy methods to conduct a scientific literature evaluate, we used these search phrases to determine related articles. As we collected educational analysis articles, our crew added extra search phrases. We then used a wide range of mixtures of the search phrases listed in Appendix B with Boolean operators to focus our outcomes. In whole, we accomplished 15 distinctive searches.
Relying on the quantity of outcomes listed in a search, we reviewed between 100 and 300 outcomes. If the variety of outcomes listed was beneath 1,000, we examined the primary 100. If the quantity of outcomes was beneath 100,000, we reviewed the primary 200; if there have been over 100,000 outcomes, we examined the primary 300. Within the evaluate course of, we assessed educational articles based mostly on their relevance to this examine utilizing the title of the article, the summary and the listed key phrases. Total, we collected 59 papers and entered the supply info right into a spreadsheet, together with the title, authors, yr the article or e-book was printed, summary, and full quotation.
Upon amassing the sources, we started reviewing every article to find out its relevance to this mission. We assessed the abstracts in additional element and skimmed via the articles to evaluate their usefulness. Of the 59 papers, we discovered 18 sources that proved considerably invaluable for this mission. Many of the excluded papers had been too technical for the aim of this literature evaluate. Whereas now we have tried to make this paper comparatively accessible, now we have supplied a listing of technical terminology and definitions in Appendix A. Whereas a few of these definitions are paraphrased, they comprise a good quantity of quoted materials to preserve integrity.
From our 18 sources, we extracted related info and information and synthesized them into the literature evaluate beneath. Utilizing the analysis questions listed above, we supplied an in depth overview of the know-how; thought-about the importance of report retaining, confidentiality, belief and authentication; and supplied a listing of examples of different authorities organizations and companies utilizing blockchain. As well as, we had been stunned to seek out a number of articles calling on the federal government to make use of these new applied sciences, and we additionally included this as a theme beneath.
Past educational articles, we reviewed a number of articles on the regarding elements of blockchain associated to environmental affect, public picture and potential backlash, a scarcity of regulation, and the potential to be blinded by the hype of blockchain know-how. We additionally researched 5 particular blockchains: Ethereum, Avalanche, Cardano, Hyperledger and Solana. The variety of blockchains accessible grows every day, however our crew selected to research these 5. Ethereum is an especially common peer-to-peer blockchain that makes use of a good quantity of vitality. Avalanche is a extra environmentally pleasant proof-of-stake blockchain, like Cardano, which can be a proof-of-stake blockchain that’s simple on the surroundings in contrast with Ethereum. Hyperledger is an umbrella mission of open-source blockchains and associated instruments, and Solana is a carbon-neutral, proof-of-stake blockchain. Extra details about these 5 blockchains and their variations is supplied beneath. This systematic literature evaluate strengthened our information of this know-how and supported us in creating really helpful options and subsequent steps for this mission, discovered beneath.
Literature evaluate
This mission goals to discover how know-how can assist customers confirm and authenticate information from the StatCan web site. This literature evaluate begins with a quick overview of cryptographic know-how. Subsequent, we think about the significance of report retaining, confidentiality, belief and authentication. We offer examples of organizations, companies and corporations in Canada that use this know-how. Then, we record a number of sources that decision on the federal government to maneuver towards new know-how akin to blockchain. Subsequent, we think about potential issues with utilizing blockchain, akin to environmental affect, public picture and potential backlash, a scarcity of regulation, and the chance of being blinded by the hype of blockchain know-how. Lastly, we evaluate 5 blockchains: Ethereum, Avalanche, Cardano, Hyperledger and Solana. This mission is a small step for StatCan towards new know-how that may higher defend its information.
Overview of the know-how
Within the early Nineteen Nineties, cryptographers Scott Stornetta and Stuart Haber conceived the thought of “connecting blocks through hashed information” (Treiblmaier and Clohessy, 2020, p. v). Virtually 20 years later, on October 31, 2008,
A mysterious particular person, or group of people, recognized solely as Satoshi Nakamoto, posted a hyperlink to a paper entitled Bitcoin: A Peer-to-Peer Digital Money System to an obscure mailing record known as Cryptography Checklist. On this paper, Nakamoto proposed the creation of what would change into often called a blockchain as a method of enabling an digital cost system that didn’t require a trusted third-party middleman (City and Pineda, 2018, p. 5).
A blockchain is “a digital, decentralized and distributed ledger by which transactions are logged and added in chronological order with the aim of making everlasting and tamper-proof information” (Treiblmaier, 2018, p. 547). The concept of the ledger has existed for a very long time—it’s a everlasting assortment of recorded transactions, traditionally written in a bodily e-book. Shifting the ledger on-line right into a digital forex is the place blockchain originated. Since then, blockchain has broadened to incorporate digital safety past digital forex akin to Bitcoin.
A lot of this know-how stems from cryptography. The time period “cryptography” is derived from the Greek phrase kryptos, which is used to explain something that’s “hidden, veiled, secret, or mysterious” (Mohamed, 2020, np). Cryptography secures communication and knowledge utilizing know-how and codes. It’s well-known that information are invaluable and infrequently weak. “In immediately’s world, producing faux paperwork is turning into extra frequent. Because the faux ones precisely appear to be the originals, it’s impractical for a standard man to determine the actual and the duplicate one” (Prathibha and Krishna, 2021, p. 71). Given this info, know-how that makes use of cryptography and blockchain can defend the knowledge, making it “tamper-resistant [and] exceptionally arduous to vary or delete” (De Filippi, 2018, p. 34–35). As individuals start to acknowledge the numerous and inherent worth of information, blockchain and distributed ledger know-how “might drive some organizations essentially to rethink their relations with customers and approaches to privateness” (Maull et al., 2017, p. 484). Earlier than offering some examples of blockchain use in Canada, we are going to talk about the significance of report retaining, confidentiality, belief and authentication for our mission.
File retaining
Victoria Lemieux, an archival research scholar, claims that “a lot of the dialogue about trusted information or methods boils down to 2 interlinking ideas: reliability and authenticity” (2016a, p. 112). When a consumer accesses a report, they think about any potential dangers related to the information (Lemieux, 2016a). Customers decide the reliability of information based mostly on how they’re accessing the information and on report creation, together with who created the report and the way (Lemieux, 2016a). Lemieux argues that “long-term preservation of data in digital type requires that technical risks to the longevity of genuine info be addressed” (2016a, p. 114). In our case, “the aim of what’s truly saved on chain … is just not archiving however slightly to determine that the unique transaction report is genuine” (Lemieux, 2016b, p. 15). The goal of this mission is to proactively safeguard StatCan information via the added worth of blockchain know-how.
Confidentiality
This mission demonstrates that StatCan acknowledges the significance of confidentiality. When coping with information, confidentiality “refers back to the safety of data, akin to laptop recordsdata or database parts, in order that solely approved individuals might entry it in a managed approach” (Mohamed, 2020, np). StatCan information should be shielded from potential threats or assaults. To perform this, we should decide the vulnerability or weak spot of the present StatCan system (Mohamed, 2020). It’s doable that information on the StatCan web site could possibly be altered with out the consumer’s information. This mission makes an attempt to repair the potential danger by addressing confidentiality and guaranteeing that info will be authenticated by the consumer.
Belief
In accordance with a chapter on how authenticity can remodel social belief, Batista et al. illustrate the three most vital elements of belief: accuracy, reliability and authenticity (2021, p. 112). They argue that “correct [and reliable] information are exact, appropriate, truthful … constant, full, and goal” (Batista et al., 2021, p. 114). To generate belief, the authors describe that genuine information must “protect their identification and integrity over the interval of long-term preservation” (Batista et al., 2021, p. 116). Within the case of digital archives, the authors describe the problem in sustaining belief with a digital doc. For instance, suppose a statistical doc has been altered. On this case, it is likely to be difficult to detect the variances between the unique and the copy that has been tampered with, and this may negatively affect social belief as a result of of what they name “unsure authenticity” (Batista et al., 2021, p. 117). This mission seeks to enhance belief between StatCan and its customers by offering a approach to authenticate information from the StatCan web site and eradicating uncertainty.
Authentication
Authentication refers back to the capacity to decide the validity of a supply. It solutions the query, “How does a receiver know that [the] distant speaking entity is who it’s claimed to be?” (Mohamed, 2020, np). On this mission, StatCan desires to assist customers decide the validity of a supply via an authentication course of. Cryptographic algorithms assist authenticated encryption, which means that customers can ensure the supply is genuine (Mohamed, 2020). This verification additionally instills integrity—it means they will know that the knowledge has not been modified until StatCan staff modified it via correct authorization (Mohamed, 2020). Evidently, report retaining, confidentiality, belief and authentication are vital components on this mission. Subsequent, we offer examples in Canada that show this know-how in use.
Begin of textual content field
- Cryptography is the method of securing communication and knowledge utilizing know-how.
- A blockchain is “a digital, decentralized and distributed ledger” (Treiblmaer, 2018, p.547).
- A blockchain can assist report retaining via archiving information, enhance confidentiality and reduce vulnerability, generate belief between the consumer and StatCan, and assist customers in authenticating information from the StatCan web site.
Finish of textual content field
Examples in Canada
Many examples had been present in our analysis of the Canadian authorities incorporating blockchain into particular initiatives. In a coverage e-book printed by the Mowat Centre for Coverage Innovation on the College of Toronto, City and Pineda (2018, p. 61–62) record many Canadian authorities companies experimenting with blockchain, akin to Innovation, Science and Financial Improvement Canada; the Treasury Board of Canada Secretariat; and the Nationwide Analysis Council Canada (NRCC). In January 2018, the Industrial Analysis Help Program within the NRCC used an Ethereum blockchain to “proactively publish grants and contribution information in real-time” (Industrial Analysis Help Program, 2019). This mission was an experiment that ran for one yr and concluded on March 1, 2019. Whereas the experiment is just not ongoing, this work has supplied “constructive perception into the potential for this know-how and the way it could also be used for extra open and clear operations for public applications” (Nationwide Analysis Council Canada, 2018).
A number of ranges of presidency have moved towards utilizing blockchain for permits, together with the Authorities of Ontario, the Metropolis of Toronto and the Authorities of British Columbia (City and Pineda, 2018, p. 62). One article lists a wide range of ways in which governments are utilizing blockchain, together with for “digital identification, the storing of judicial choices, financing of college buildings and tracing cash, marital standing, e-voting, enterprise licenses, passports, legal information and even tax information” (Ølnes, Ubacht, and Janssen, 2017, 357). The Authorities of Ontario additionally “ran a blockchain hackathon that generated quite a few concepts for different blockchain purposes in authorities” (City and Pineda, 2018, p. 62). Supporting pilot initiatives that use blockchain is an efficient approach for the federal government to start utilizing these new applied sciences efficiently (City and Pineda, 2018, p. 67). Governments are utilizing blockchain in lots of areas, and StatCan can use this data and construct upon their work on this mission.
Along with authorities companies implementing blockchain and distributed ledger know-how, well being care is transferring quickly towards blockchain and digital well being care information. Storing digital well being information on a blockchain is just not solely bettering report retaining but additionally “giving sufferers larger management over their very own well being and medical therapies” (City and Pineda, 2018, p. 42). Docs, nurses, hospitals and different well being care establishments are utilizing blockchain to certify the well being of sufferers (De Filippi, 2018, p. 112). It’s getting used to “retailer encoded private well being information” (Zheng, Zhu, and Si, 2019, p. 17). The blockchain can present entry to particular people, so an individual’s well being information will be safe and confidential when saved in a distributed ledger (Zheng, Zhu, and Si, 2019). Lemieux writes, “the underlying situations in Canada are notably well-suited to main blockchain analysis and implementation … Canada has a vibrant, extremely energetic blockchain technoscape, with a range of start-ups and consultancies doing modern work” (2016b, p. 5). We’re excited so as to add to this work in our mission.
Begin of textual content field
- Blockchain is being utilized by a number of ranges of presidency in Canada, together with the Authorities of Ontario, the Metropolis of Toronto and the Authorities of British Columbia.
- Well being care in Canada has additionally begun to make use of blockchain and distributed ledger know-how to securely retailer digital well being care information.
Finish of textual content field
Name to motion
A number of papers known as on governments to maneuver towards new know-how to raised safe their information. City and Pineda argue that blockchain can “supply governments the opportunity of improved transparency, effectivity, and effectiveness” (2018, p. 42). Whereas blockchain is just not a new know-how, its use in authorities is comparatively new, so “the extent of blockchain experience and capability inside Canadian governments and regulators is at present restricted” (City and Pineda, 2018, p. 61). They declare that considered one of the primary issues the Canadian authorities ought to do is what we’re doing at present on this mission: “increase teams of technologists and policymakers inside authorities who perceive the know-how, its implications, and the potential alternatives and challenges that circulate from it” (City and Pineda, 2018, p. 61). Whereas City and Pineda (2018) are pushing for extra blockchain in authorities, Ølnes, Ubacht and Janssen emphasize that the authorities ought to “shift from a technology-driven to want pushed method with blockchain purposes” (2017, p. 355). They argue that blockchain “will result in innovation and transformation of governmental processes” (Ølnes, Ubacht, and Janssen, 2017, p. 355). Contemplating “the convenience with which digital recordsdata will be altered” (Bell et al., 2019, p. 6), we argue that this mission is pushed by a necessity for authentication on the StatCan web site.
In accordance with De Filippi, “governments have established and stewarded a wide range of methods and establishments designed to reinforce social welfare and supply the foundational infrastructure for financial and political progress” all through historical past (2018, p. 107). In an article on cryptography and authorities, Aljeaid et al. argue that “e-government … acts as a communication bridge … between authorities to citizen, or authorities to authorities, or authorities to enterprise in environment friendly and dependable methods” (2014, p. 581). The authors emphasize the significance of information safety in authorities associated to potential vulnerability if left unsecured. They declare that “finish customers want sturdy safety options to attain assurance when coping with e-government methods” (Aljeaid et al., 2014, p. 581). Making a “tamper-resistant and resilient repository for public information” (De Filippi, 2018, p. 107–108) utilizing cryptography and blockchain can assist the federal government keep away from information leaks, information loss and different vulnerabilities. We agree with this name to motion and imagine that this mission will enhance public belief in StatCan and the Authorities of Canada.
Begin of textual content field
- A number of authors are calling on the Canadian governments to maneuver towards utilizing new know-how, akin to blockchain, to raised safe their information.
- This know-how can assist the federal government keep away from information vulnerabilities and enhance transparency, safety, effectivity and effectiveness.
Finish of textual content field
Concern
Whereas the decision to motion is important, we additionally wish to take the time to research any potential issues concerning blockchain. Now we have summarized our findings into 4 classes: environmental affect, public picture and potential backlash, a scarcity of regulation, and the potential to be blinded by the hype of blockchain know-how.
Environmental affect
There have been many claims in regards to the environmental affect of recent blockchain know-how. In November 2021, a blockchain mission known as Solana contracted Robert Murphy, a local weather and vitality advisor, to publish an vitality use report (Solana, 2021). They in contrast frequent actions that contain vitality consumption with one Solana transaction, one Ethereum transaction and one Bitcoin transaction (Solana, 2021). Whereas they didn’t embrace all of the blockchain choices that now we have chosen to research, it’s useful to think about how blockchain transactions evaluate with on a regular basis actions. Conducting a single Google search makes use of 1,080 joules of vitality, engaged on a pc with a monitor for an hour makes use of 46,800 joules, and utilizing one gallon of gasoline makes use of 121,320,000 joules (Solana, 2021). By comparability, one Solana transaction makes use of 1,837 joules of vitality, one Ethereum transaction makes use of 692,820,000 joules, and one Bitcoin transaction makes use of 6,995,592,000 joules (Solana, 2021). In accordance to Huang, O’Neill, and Tabuchi for The New York Occasions, “the method of making Bitcoin to spend or commerce consumes round 91 terawatt-hours of electrical energy yearly, greater than is utilized by Finland, a nation of about 5.5 million” (2021). Whereas we’re not utilizing Bitcoin for our mission, these numbers are staggering.
Most of the large gamers in blockchain, together with Ethereum, are utilizing an astonishing quantity of vitality due to their proof-of-work (PoW) consensus mechanism. PoW requires community members on the blockchain “to expend giant quantities of computational assets and vitality on producing new legitimate blocks” (Chandler, 2021). As compared, proof of stake (PoS) requires community members on the blockchain “to stake cryptocurrency as collateral in favor of the brand new block they imagine needs to be added to the chain” (Chandler, 2021). Chandler argues that PoW, akin to Ethereum, will be extra safe and decentralized, but additionally makes use of an immense quantity of electrical energy, is slower and is much less scalable (Chandler, 2021). Against this, PoS, akin to Avalanche, Cardano and Solana, has a smaller environmental affect and permits for sooner transactions and higher scaleability, however it’s a newer type of know-how and “will not be as safe or tamper-resistant as proof of labor” (Chandler, 2021). Evidently, each PoS and PoW have benefits and downsides, and we think about the precise environmental affect of 5 blockchains (Ethereum, Avalanche, Cardano, Hyperledger and Solana) within the chart beneath.
Public picture and potential backlash
There have been a number of examples of firms and organizations that acquired backlash when making an attempt to make use of blockchain. In December 2021, Kickstarter introduced that it was transferring to blockchain (Plunkett, 2021). The weblog submit, titled “Let’s Construct What’s Subsequent for Crowdfunding Artistic Initiatives,” acquired many critiques and complaints from creators (Plunkett, 2021). Kickstarter responded by offering a ceaselessly requested questions part, the place it claims it’s “assured {that a} crowdfunding protocol constructed on high of Celo won’t considerably negatively affect our carbon emissions given its underlying structure” (Kickstarter, 2022). Nonetheless, many creators and backers have claimed that they’ll now not be utilizing Kickstarter, given this info (Morse, 2021).
Just like Kickstarter, the digital communication platform Discord tweeted about integrating Ethereum into its platform in November 2021 (Pearson, 2021). The founder and chief government officer of Discord, Jason Citron, rapidly backed off the mission two days later, after public backlash (Pearson, 2021). Pearson states that individuals within the sport business hate blockchain “both due to the environmental affect of proof-of-work tokens on Ethereum, the concept blockchain collectibles are a grift based mostly on legendary pondering, or each” (2021). Many customers unsubscribed from the platform’s premium “Nitro” paid service or threatened to take action (Jiang, 2021). Provided that each of those examples happened not too long ago, in November and December 2021, it’s tough to contemplate what the general public opinion is likely to be concerning StatCan and this mission. Nonetheless, you will need to concentrate on these examples and acknowledge that backlash is a possible end result.
Lack of regulation
One other concern is the decentralized and unregulated nature of blockchain. Provided that management and choice making about the blockchain is just not carried out by a single entity, that is an space of concern for StatCan. Moderately than placing belief in a single entity, belief is put in mathematical algorithms. Provided that there have been different blockchain initiatives by Canadian governments, they need to be used as a information for StatCan insurance policies concerning this mission. Between the 5 blockchains we take a look at beneath, every has completely different rules, targets and skills. It can be tough to scale, relying on the blockchain chosen. This can be a priority as a result of it has not but been determined what number of StatCan merchandise shall be accessible for authentication. Since we checked out belief and confidentiality earlier on this literature evaluate, the dearth of regulation is much less worrisome than the affect on the surroundings and public picture. In reality, this mission is a chance to be an early instance and chief in blockchain implementation rules, and we hope that we will incorporate new insurance policies into our mission.
Blinded by the hype
The general hype of blockchain know-how must be addressed. In accordance with Victoria Lemieux, we have to “tackle the shortcomings in designs and implementations of blockchain report retaining in order to be higher in a position to understand the worthy imaginative and prescient of blockchains” (Lemieux, 2019). She writes, “claims related to use of blockchain know-how for recordkeeping are, in quite a few instances, overhyped. For instance, blockchain options that declare to offer ‘archival’ options don’t truly protect or present for long-term accessibility of information” (Lemieux, 2016b, p. 4). She claims that the largest hazard in blockchain comes from blindly trusting it (2016b, p. 23). Nonetheless, critically investigating these limitations is the “key to efficiently leveraging technological improvements just like the blockchain for the good thing about all Canadians” (Lemieux, 2016b, p. 8). Whereas blockchain know-how doesn’t remedy each downside that it has been claimed to, it’s a helpful know-how that “will proceed for use in business and is deserving of additional analysis and experimentation” (Ruoti et al., 2020, p. 53). Whereas this comparatively new know-how is thrilling, and contemplating dangers can deliver up “fears of stifling innovation” (Lemieux, 2016b, p. 5), it’s crucial that we’re crucial of the potential limitations and issues about blockchain know-how to have the very best end result on this mission.
Begin of textual content field
- There are 4 issues concerning using blockchain:
- Environmental affect associated to vitality consumption, with completely different blockchains utilizing completely different quantities of vitality
- Potential backlash based mostly on the expertise of firms that attempted to maneuver towards blockchain and had been critiqued by their customers
- Normal lack of regulation as a result of of the decentralized nature of blockchain
- Changing into blinded by the hype of blockchain know-how.
Finish of textual content field
5 blockchains: Ethereum, Avalanche, Cardano, Hyperledger and Solana
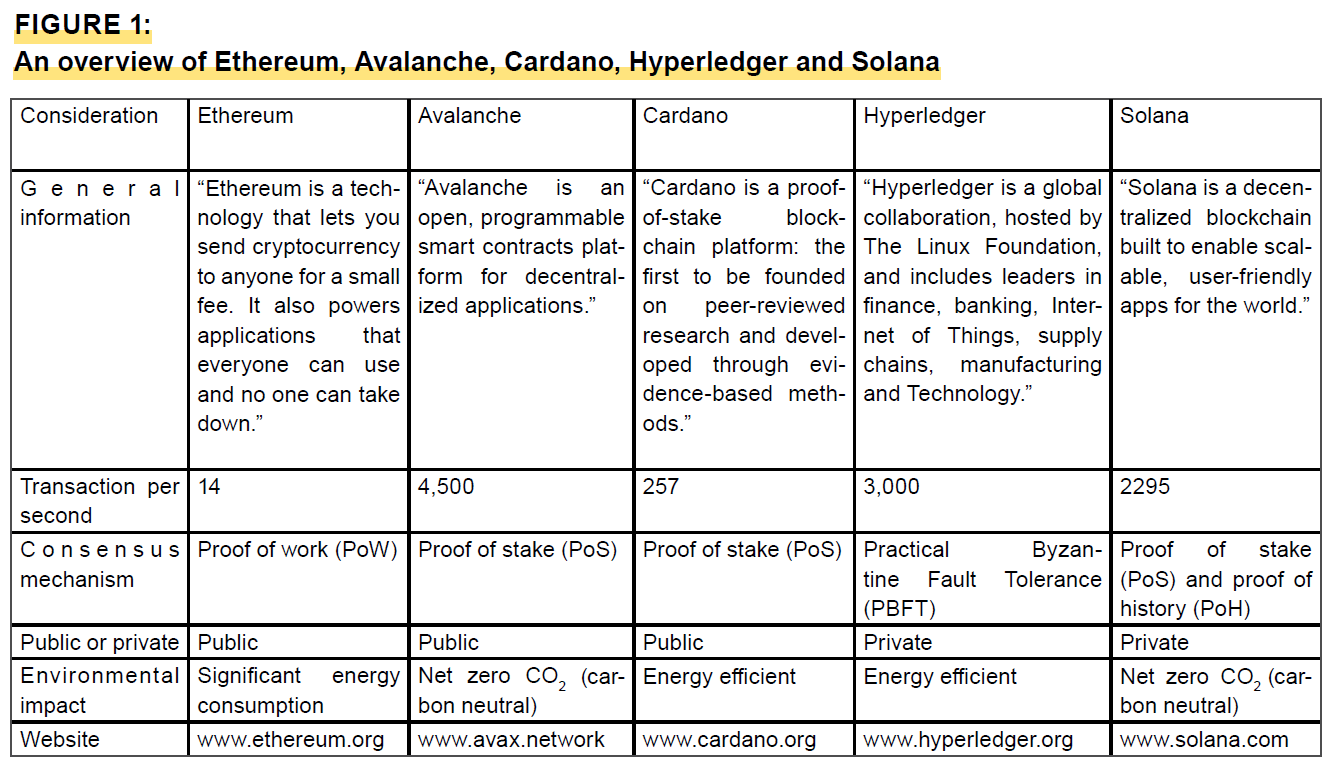
For this mission, we selected to guage and evaluate 5 completely different blockchains, with particular issues. We determined to take a look at Ethereum, Avalanche, Cardano, Hyperledger and Solana. Ethereum is one of the most well-liked blockchains, but it conducts the fewest transactions per second and has vital vitality consumption in contrast with different choices as a result of it makes use of proof of labor (PoW). PoW signifies that a majority of customers must vote on every new blockchain, and this takes extra effort and time than proof-of-stake (PoS) blockchains. We additionally included Avalanche and Cardano, that are each PoS public blockchains. Whereas Avalanche’s environmental affect is carbon impartial, its transaction fee per second is the best, in contrast with the opposite 4 blockchains we analyzed. In the meantime, Cardano is much less vitality environment friendly and slower than Avalanche. We additionally selected to incorporate Hyperledger, as it’s a non-public blockchain that makes use of Sensible Byzantine Fault Tolerance as its consensus mechanism. It’s a non-public blockchain, which signifies that it’s centralized. This doubtlessly impacts belief, as fewer nodes could make the community much less safe. Lastly, we included Solana as a result of it’s carbon impartial, makes use of PoS and has supplied a report on vitality consumption compared with blockchains akin to Ethereum. All the blockchains outlined beneath have benefits and disadvantages. Upon reviewing them, now we have determined to make use of Avalanche for this mission. Avalanche is an open-source PoS blockchain with the best transaction fee per second, at 4,500. Moreover, it’s a public community that’s carbon impartial, an vital consideration for us.

Description of determine 1
Determine 1 shows an outline of 5 blockchains in a chart: Ethereum, Avalanche, Cardano, Hyperledger and Solana. Within the chart, we offer common details about every blockchain, the transaction per second fee, the kind of consensus mechanism that every blockchain makes use of, whether or not the blockchain is public or non-public, and the environmental affect of every blockchain. We additionally embrace a hyperlink to the web site for every blockchain.
Begin of textual content field
- Our mission is transferring ahead with Avalanche, which is an open-source proof-of-stake blockchain with the best transaction fee per second, at 4,500.
- It’s a public community and carbon impartial, resolving considered one of our issues listed above, concerning environmental affect.
Finish of textual content field
The technical answer
Our analysis crew has designed an answer that incorporates blockchain know-how utilizing the information gained from our literature evaluate and pre-existing technical expertise. This part outlines system particulars and the really helpful answer for enabling customers to authenticate paperwork downloaded from the StatCan web site. We are going to start by introducing three technical parts which might be the pillars of our answer: digital signatures, hash features and safe tunnels. These three technical parts work together as follows: a hash computed over the file that belongs to StatCan is used to verify the file has not been tampered with; a digital signature over this hash proves that the file is owned by StatCan, and the safe tunnel ensures safe communication between the consumer and the StatCan web site. On this part, we clarify how these constructing blocks work and the way they’re built-in into our proposed options.
Digital signatures
When customers obtain a file from the StatCan web site, there are two questions that they could have. First, do the information truly belong to StatCan? And second, have the information been tampered with?
Query 1: Does the information truly belong to StatCan?
To deal with this query, we suggest utilizing a digital signature. The concept is just like signing a doc with a pen—when you obtain a signed letter or doc from “x,” you possibly can test whether or not the signature on the doc belongs to “x” and consequently whether or not the doc is theirs. In a digital signature scheme, a private-public key pair is used to signal a doc and confirm the signature over a doc’s hash. There are three steps to a digital signature scheme: StatCan must (1) generate the public-private key pair, in order that (2) it will probably signal the hash of the doc with its non-public key, and (3) any consumer with the general public key can confirm the signature.
Step 1: Key era.
Utilizing a operate that generates keys, StatCan can receive a public-private key pair. The general public secret’s shared on the web site for customers to obtain and use in the course of the signature verification. StatCan wouldn’t share the non-public key, as it’d result in a malicious actor utilizing the non-public key to forge StatCan’s signature on paperwork. It’s vital to notice that key era is a one-way operate, which signifies that it’s infeasible to compute the non-public key, given the general public key. StatCan would use its non-public key to generate the signature over a doc’s hash slightly than the doc itself, as it’s sooner and extra environment friendly, and the ensuing signature is shorter. Think about the signature era as a operate that asks the consumer to offer their non-public key and hash of the doc and generates a file that accommodates the signature.
Step 2: Signing the hash of a doc
To create the signature, StatCan wants its non-public key and the hash of the doc. It’s infeasible to compute a signature on the hash of a doc if the non-public key is just not recognized. The ensuing signature is saved in a separate file. StatCan would add the signature file and its public key on its web site, in order that customers can obtain (1) the file they wish to use, (2) the signature file created over the hash of that doc and (3) StatCan’s public key. Think about the signature verification as a operate that asks the consumer to offer the three recordsdata that they downloaded from the web site.
Step 3: Verifying a signature
Any consumer can confirm the validity of the signature by offering (1) the file they wish to test, (2) the signature file created over the hash of that doc and (3) StatCan’s public key. If the signature is verified, the consumer can ensure that the file truly belongs to StatCan.
Begin of textual content field
- A digital signature is an digital signature that’s generated and verified by public key encryption.
- In a digital signature scheme, StatCan must (1) generate the public-private key pair, in order that (2) it will probably signal the hash of the doc with its non-public key, and (3) any consumer with the general public key can confirm the signature.
Finish of textual content field
How can customers make it possible for they use StatCan’s key?
Public key infrastructure binds public keys with identities. That is accomplished via a registration course of the place a certification authority (CA) points certificates by signing StatCan’s public key. In consequence, a CA verifies that the general public key actually belongs to StatCan. CAs are entities that challenge certificates used to confirm the possession of a public key. Any consumer with entry to the CA’s public key can confirm the certificates issued over StatCan’s public key. The certificates are legitimate for a particular period of time.
Hash features
Query 2: Has the information been tampered with?
Hash features are used to create a novel fingerprint for the enter message. This know-how offers StatCan the flexibility to hash a doc (akin to a CSV file) and create a novel “fingerprint” of it in the type of a fixed-size hash. As soon as StatCan computes the hash of the file, it uploads it to the web site. When customers obtain a file, the doc is hashed. The ensuing hash is in contrast with the uploaded worth to make it possible for the file has not been tampered with. This a part of the method is dealt with by the appliance itself. We are going to clarify this in additional element within the proposed options.
Begin of textual content field
- Hashing is a time period that refers to using an algorithm, known as a hash operate, to transform a bit of info into an alphanumeric string of characters.
Finish of textual content field
To unravel customers’ concern in regards to the authentication of their downloaded file, together with digital signatures, we should use hash features in our answer. That is frequent observe in cryptography, as hash features are recognized to be safe (Al-Kuwari, Davenport, and Bradford, 2011). They’re used towards malicious events that will attempt to change information intentionally. Utilizing hash features fills a requirement in our proposed system, as a result of an attacker shouldn’t be in a position to create a file with a selected hash and change it with a file from StatCan. For the hash features to function successfully, they require sure properties. For instance, when two individuals hash the identical doc utilizing the identical hash operate, they get the identical hash worth. The hash operate produces the identical output for a given enter (which can be known as “pre-image”); because of this hash features are deterministic. Even when a single letter is added to a single cell within the doc, the ensuing hash shall be completely different (see Determine 2). The determinism property is related in the context of guessing the pre-image. Enter to the hash operate can’t be computed by simply trying on the hash worth. Nonetheless, one can attempt to guess the pre-image, hash it and evaluate it with the hash worth. Think about consumer authentication—passwords are usually saved as hashes. If an attacker can entry this database of hashes, they will decide a password (for instance, considered one of probably the most generally used passwords), hash it and evaluate it towards the database to see whether or not there’s a match.
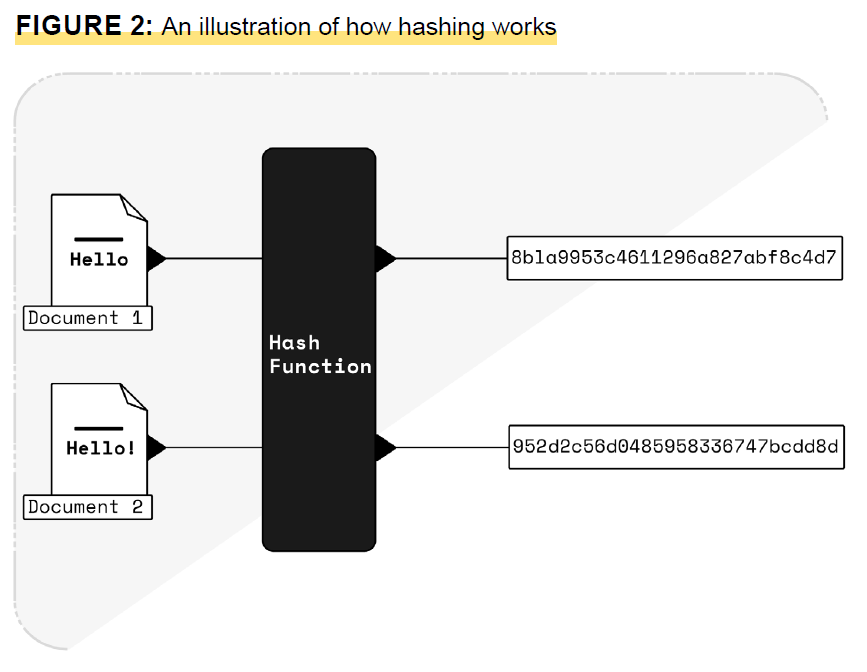
Description of determine 2
Determine 2 is an illustration of how hashing works. The picture reveals a doc with the phrase “Howdy,” pointing towards a centre black field with the phrases “hash operate.” On the proper aspect of the picture, there’s a randomly generated record of numbers and letters. Under, there’s a doc with the phrase “Howdy!” pointing towards the hash operate black field. As a result of this doc contains an exclamation mark, the hash output is distinct as properly. When a doc is hashed, a fixed-size output is created. Every distinct doc has its personal distinct output, even when solely a single character is completely different.
Word: This picture illustrates how hashing works. Doc 1 accommodates the phrase “Howdy”, and the hash operate creates “Hash 1” over this doc. The second doc differs from Doc 1 by one character: “Howdy!” The hash operate creates “Hash 2” over Doc 2. Hash 1 and Hash 2 have completely different values, as Doc 1 and Doc 2 are completely different. Hash 1 and Hash 2 are the identical measurement, as the hash operate produces fixed-size outputs.
Most related to our mission, it’s crucial to notice that we anticipate a hash operate to have the collision resistance property, which means that it’s infeasible to seek out any two completely different messages which have the similar hash. In different phrases, an adversary can’t discover one other CSV file with completely different content material that has the identical hash as the unique doc and can’t change the unique doc with one other one.
For the sake of a complete understanding, we should additionally point out the opposite two properties {that a} hash operate ought to have. To make sure readability, notice {that a} message to be hashed is called the pre-image, and the ensuing hash is called a picture. “Pre-image resistance” implies that given the hash of a message, it’s infeasible to discover a corresponding message. “Weak collision resistance” states that given a message, it’s infeasible to seek out one other message with the identical hash. As beforehand talked about, the hash operate can be wanted for the signing operation. StatCan indicators the hash of the doc, slightly than the doc itself, to have a shorter signature. This will increase effectivity, as signing the hash is way sooner. Since the hash is used within the signature operate, we’d like the collision resistance property.
There are well-known hash features, akin to MD 5, SHA1, SHA2 and SHA3. Nonetheless, not all are safe. MD 5 and SHA1 are confirmed to be insecure, as they don’t have the collision resistance property. Whereas it takes longer to assault SHA1 than MD 5, each are at present thought-about weak. Hash features can break over time, however they get changed with safe ones. For now, we all know that SHA2 and SHA3 are safe (Nationwide Institute of Requirements and Expertise, 2015). As SHA3 is safer than SHA2, we suggest utilizing SHA3 in our answer.
Begin of textual content field
- Ought to checksums be used as an alternative of hash features? Checksums are truncated hashes, and they aren’t primarily safe; checksums are used to detect random faults. An adversary can manipulate checksums to vary the information whereas guaranteeing the checksum doesn’t change. Not like hash, creating information (akin to a file) with a selected checksum is just not tough. This property prevents the detection of errors. For these two causes, checksums can’t defend towards malicious adversaries.
- Error-correcting code is used to detect errors in the course of the transmission of information over an unreliable channel. The message is encoded with redundant info. The receiver makes use of this redundant info to detect a restricted variety of errors. These errors will be corrected inside sure limits. The errors will be corrected on the receiver aspect (i.e., retransmission of information is pointless).
Finish of textual content field
Safe tunnels
The proposed options require a safe tunnel between the consumer and the StatCan web site for communication. In each the offline and hybrid options discovered beneath, the consumer has to obtain an utility from the StatCan web site. The consumer has to verify they get the precise utility, and a safe tunnel is required between the consumer and StatCan for that goal. Additionally, within the on-line answer, the consumer communicates with the StatCan web site utilizing the safe tunnel. “Https” gives a safe tunnel, which means that if an attacker observes the visitors within the tunnel, they won’t know the content material of the message being transmitted. All an attacker can observe is that there’s visitors between two events.
The safe tunnel gives
- message confidentiality—because the messages being transmitted are encrypted, an attacker can’t decipher them to learn the content material (they know solely that there’s a message transmission between two events)
- message integrity: an attacker on the trail is just not in a position to modify the visitors
- server authentication: it’s recognized the place the tunnel ends, and it doesn’t result in the adversary.
Three potential options
There are three potential options that might be applied utilizing the beforehand talked about know-how to resolve consumer wants to authenticate a StatCan doc. Offline and hybrid options require the creation of an utility that’s downloaded by the consumer. In these options, the consumer interacts with the appliance to test the validity of a doc.
1. Offline answer
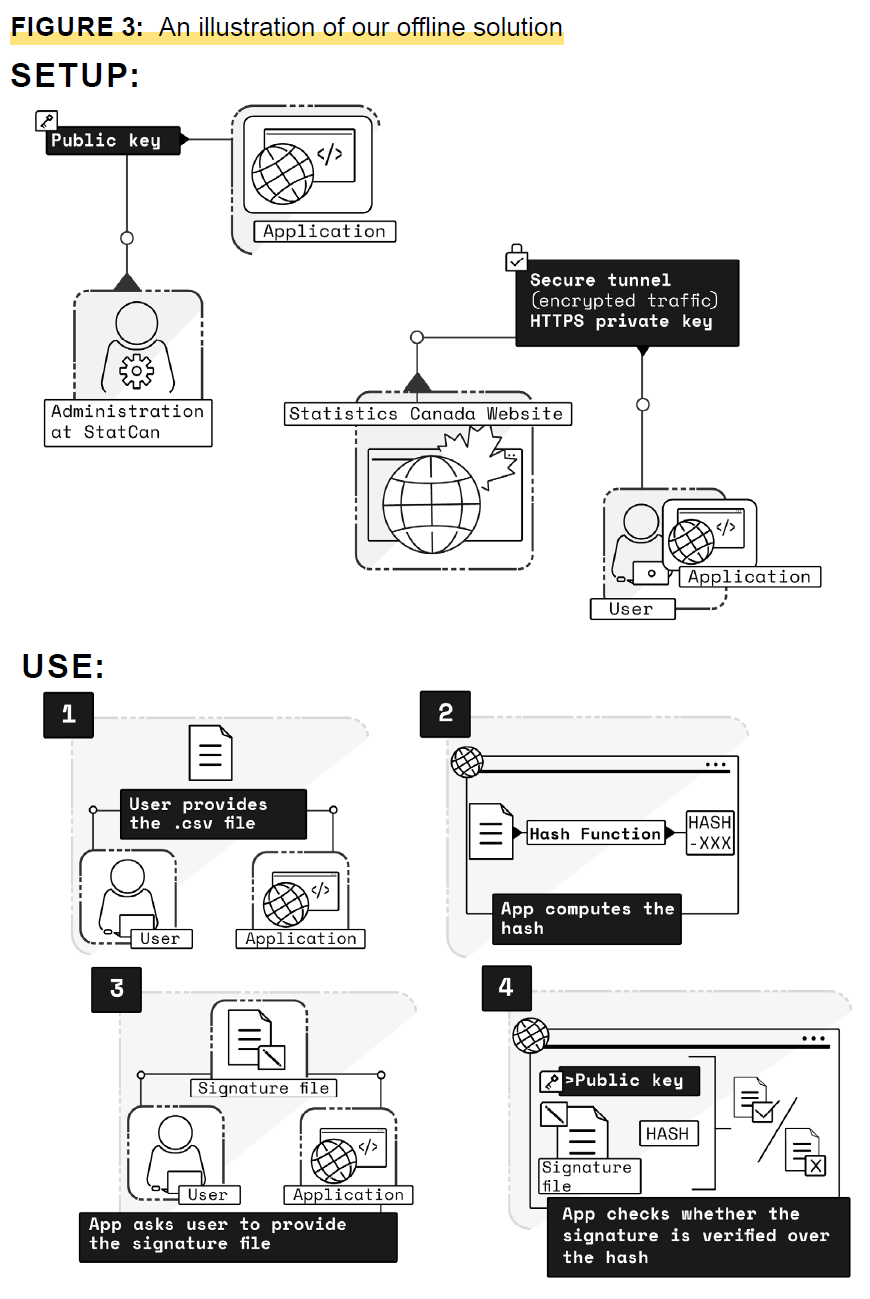
Description of determine 3
Determine 3 is an in depth picture of our offline answer. It shows the setup of the answer, which incorporates how Statistics Canada will hard-code the keys into the appliance, and an illustration of the safe tunnel between Statistics Canada and the appliance. The determine continues onto the subsequent web page and shows how the answer is used. This part includes a consumer importing a .csv file to the appliance, the appliance computing the hash, the consumer offering the signature file to the appliance and the appliance checking whether or not the signature is verified over the hash.
On this answer, the consumer downloads an utility from the StatCan web site via the safe tunnel. This allows the consumer to make sure that the appliance they obtain belongs to StatCan. The utility checks the validity of the consumer’s doc. The consumer takes the CSV file and signature file they downloaded from the web site collectively, then drags and drops the CSV file into the app. The app computes the hash over the file, then prompts the consumer to offer the corresponding signature file computed over the hash of the CSV file. The appliance checks whether or not the signature is verified over the hash. To take action, the StatCan keys have to be hard-coded into the app (setup part in Determine 3). The bottom line is wanted to confirm the signature over a file.
2. On-line answer
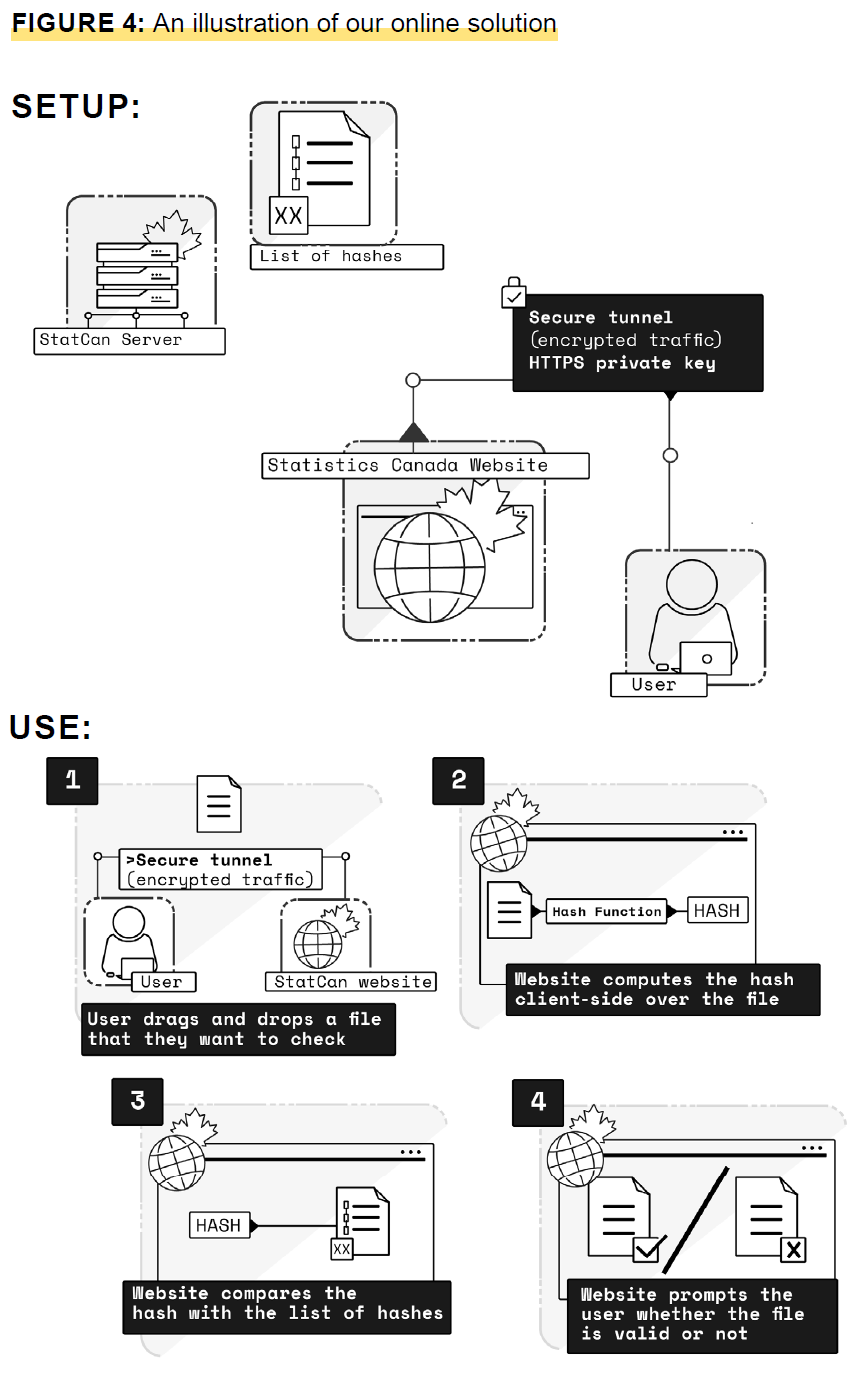
Description of determine 4
Determine 4 is an in depth illustration of our on-line answer. On this picture, the setup includes the record of hashes on the Statistics Canada server and a safe tunnel between the Statistics Canada web site and the consumer. Then, the determine shows using the net answer, which includes the consumer dragging and dropping a file they wish to test into the Statistics Canada web site via the safe tunnel. Subsequent, the web site computes the hash client-side over the file. Then, the web site compares the hash with the record of hashes, and eventually, the appliance prompts the consumer whether or not the file is legitimate.
On this answer, StatCan maintains a web page on its web site for the consumer to test doc validity. The consumer communicates with the StatCan web site utilizing the safe tunnel, and so they drag and drop a file that they wish to test. For the reason that web site is aware of the record of hashes of all recordsdata, it will probably compute the hash consumer aspect over the file supplied by the consumer and evaluate it with the record; StatCan maintains a server the place the record of hashes is saved. The consumer then learns whether or not the file they uploaded is legitimate. If legitimate, the file has not been tampered with and belongs to StatCan. In contrast with the offline answer, this method provides a extra easy expertise for the consumer, as they solely have to offer the product’s file. Nonetheless, this answer requires the consumer to be on-line, in contrast to the earlier utility that runs offline.
3. Hybrid answer
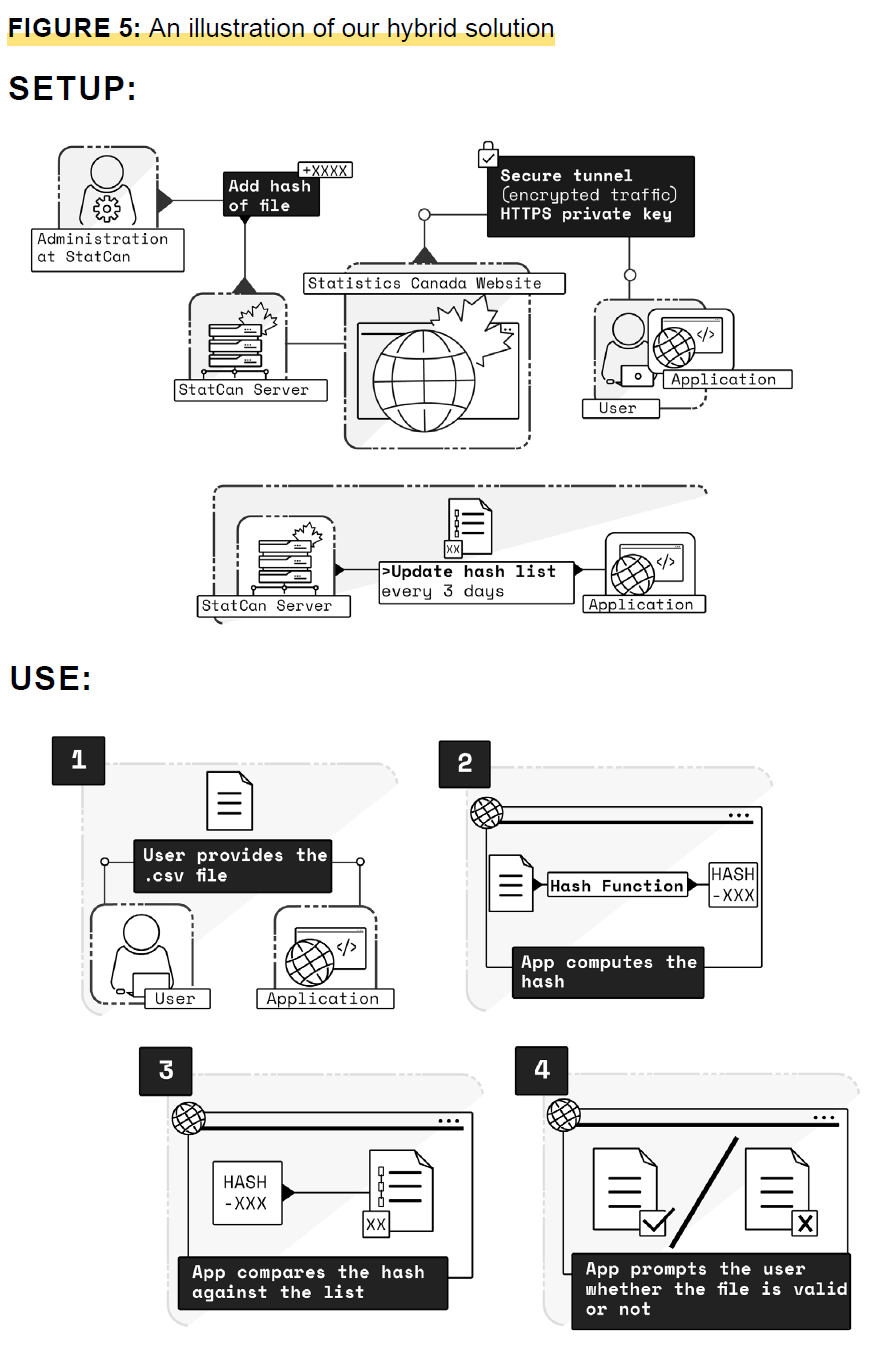
Description of determine 5
Determine 5 is an in depth illustration of the hybrid answer. On this picture, the setup is extra advanced. Statistics Canada provides file hashes to the Statistics Canada server, which then get pushed to the web site and utility via a safe tunnel. The Statistics Canada server updates the record of hashes each three days. There may be an illustration beneath of how the hybrid answer is used. It reveals how the consumer uploads the .csv file to the appliance, how the appliance computes the hash, then how the appliance compares the hash towards the up to date record of hashes, and eventually how the appliance prompts the consumer whether or not the file is legitimate.
Within the hybrid answer, the consumer should obtain an utility (just like the offline answer) over the safe tunnel. The app has a listing of hashes of recordsdata that belong to StatCan. To authenticate the doc, the consumer uploads the file to the app, which computes the hash and compares it with the record. Then, the app informs the consumer whether or not the file is legitimate. The app sometimes connects to the StatCan web site to replace the record of hashes; StatCan maintains a server the place the record of hashes is saved. Whereas we propose that the app join each three days, the period will be larger or shorter, relying on how ceaselessly StatCan shares recordsdata. Each three days, the app receives the up to date record of hashes that’s saved on the server to have the most up-to-date record. A signature over a hash proves possession. Receiving the record of hashes over the safe connection signifies that StatCan is the proprietor of the hashes. This answer eliminates the step of offering the signature file, if the hash of the file that the consumer provides seems within the record of hashes. If the hash is just not within the record, the app prompts the consumer to offer the signature file over the hash, so the app can compute the hash and confirm the signature over the file. This example may happen if a consumer tries to authenticate a file earlier than the app has the chance to hook up with the StatCan web site and replace the record of hashes.
Advisable answer
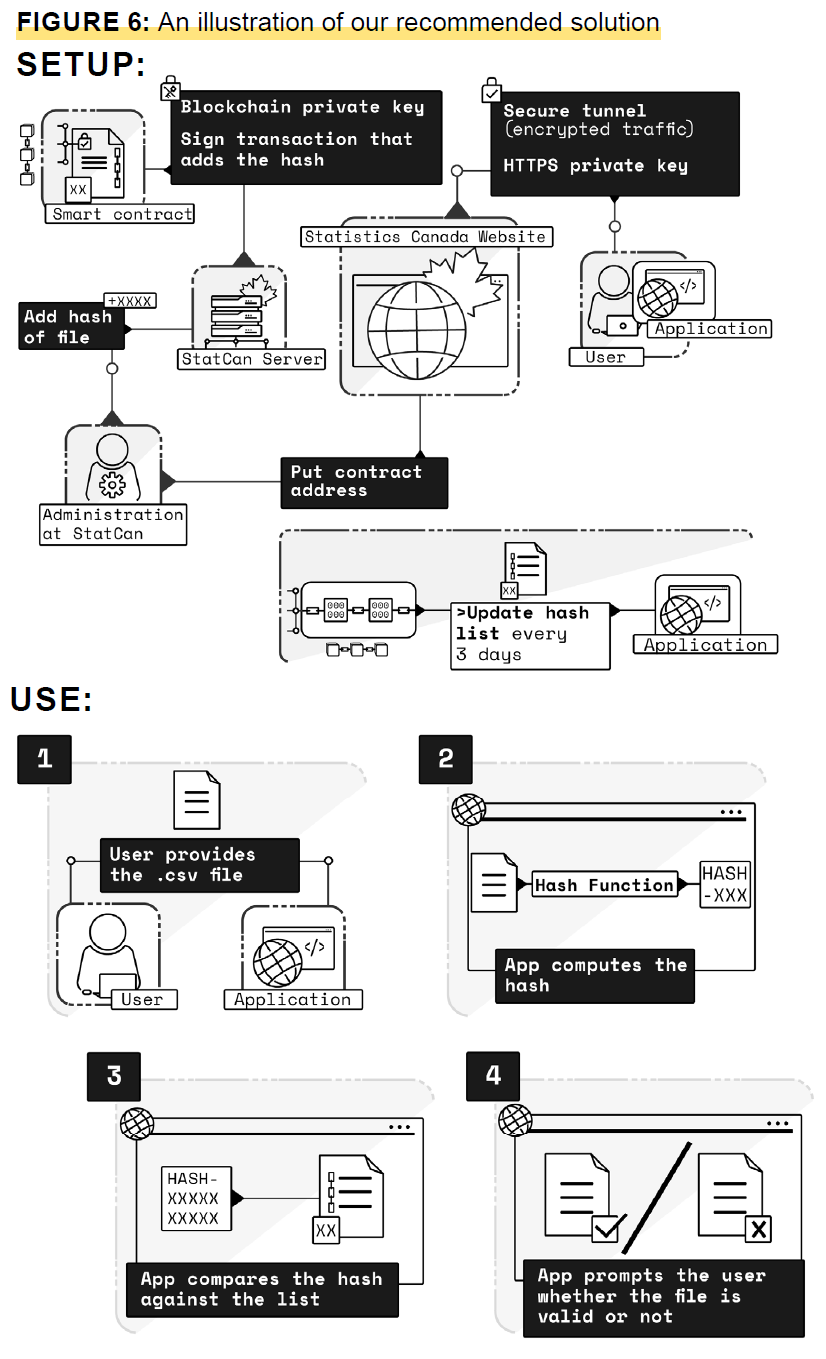
Description of determine 6
Determine 6 is an in depth illustration of our really helpful answer, which is the hybrid answer with the addition of blockchain. For the setup, Statistics Canada provides the hash of the file to the Statistics Canada server, and it’s logged on the blockchain. This, in flip, will get pushed to the Statistics Canada web site after which via a safe tunnel to the appliance. The record of hashes is up to date each three days within the utility. Within the illustration of how the hybrid answer is used, the consumer uploads the .csv file to the appliance, the appliance computes the hash, then the appliance compares the hash towards the up to date record of hashes, and eventually, the appliance prompts the consumer whether or not the file is legitimate. The picture of the consumer’s expertise is similar as Determine 5. It reveals how the consumer uploads the .csv file to the appliance, how the appliance computes the hash, then how the appliance compares the hash towards the up to date record of hashes, and eventually, how the appliance prompts the consumer whether or not the file is legitimate.
All three options supply customers the alternative to authenticate information from the StatCan web site. Nonetheless, they don’t all equally meet the requirements we set in our aims for the mission. Whereas the offline answer meets our goal of permitting customers throughout the digital divide to authenticate information, it requires the consumer to submit the corresponding signature file to the app. With regard to the net answer, the consumer solely wants to offer the CSV file, minimizing the variety of downloads for the consumer. Subsequently, the net answer provides higher usability in contrast with the offline answer. Nonetheless, the net answer doesn’t meet the requirement to present an accessible methodology of authentication, whatever the consumer’s entry to the Web.
For these causes, now we have determined that the hybrid answer is right as a result of it gives a usability degree akin to the net answer and doesn’t require the consumer to be on-line to test the file they’ve. This answer addresses the limitations mentioned above concerning constant entry to the Web. Including blockchain to the hybrid answer gives enhancements; it impacts a subcomponent of the proposed answer—the approach the hash of a file is saved. StatCan creates the hash of a file and logs this hash on the ledger. In comparison with Determine 5, the hashes are logged on the blockchain, and the app receives the up to date record of hashes from it. The added factor of blockchain will increase belief between StatCan and the general public: StatCan can’t change the information as soon as it’s posted. If StatCan adjustments the information, a historical past of that change is recorded. One other advantage of together with blockchain is that hashes can nonetheless be reached if the StatCan web site is down, as they’re recorded on the blockchain. Blockchain additionally provides higher archival properties, because it ensures that the recorded information are reachable over an extended interval than if the information are saved on a server. The server might go down or will not be constantly maintained, making the information unreachable. Blockchain gives provenance over the information (hash of the file) for a very long time, however doesn’t truly archive recordsdata. A doable disadvantage of incorporating blockchain into the hybrid answer is that if the ledger nodes manipulate the record of hashes, StatCan can’t do something about it—a world community has management over the information. Ledger nodes are the entities on this community that settle for or reject a block of transactions based mostly on their validity; they broadcast these transactions so all of the nodes keep updated. Nonetheless, within the hybrid answer with out blockchain, StatCan maintains unique management.
Begin of textual content field
- Our really helpful answer is a hybrid answer with blockchain.
- Within the hybrid answer with blockchain, authentication will happen via an utility that customers should obtain, like within the hybrid answer. The distinction is that the record of hashes of recordsdata shall be logged on the blockchain. This record shall be up to date periodically with the hashes of recent StatCan merchandise. The authentication of a file will happen as follows: the consumer might want to add the file that requires authentication to the app. This motion will immediate the app to compute the hash of this file and evaluate it with the record of present hashes from StatCan merchandise. The app receives this record of hashes from the blockchain. The app will then inform the consumer whether or not the file is legitimate.
Finish of textual content field
Appendix A: Terminology
Blockchain
- “Distributed, peer-to-peer system for validating, time-stamping, and completely storing transactions on a distributed ledger that makes use of cryptography to authenticate digital asset possession and asset authenticity, and consensus algorithms so as to add validated transactions to the ledger and to make sure the continued integrity of the ledger’s full historical past” (Lacity, 2018, p. 41).
- Blockchain is digital and decentralized, and its aim is to create “everlasting and tamper-proof information” (Treiblmaier, 2018, p. 547).
- In accordance with A. Welfare (2019), blockchain has 5 vital traits: fact and belief, transparency, safety, certainty, and effectivity.
- In computing, a blockchain is “a sequence of digital information or ‘blocks’ linked utilizing cryptography so that every block is verifiable and just about unchangeable, which is distributed and managed usually in a peer-to-peer community” (OED, n.d.a).
Certification authority
- The Pc Safety Useful resource Middle (CSRC) defines a certification authority as “an entity approved to create, signal, challenge, and revoke public key certificates” (n.d.a).
Checksum
- The Oxford English Dictionary defines checksum as “a sum calculated from the digits in a set of information and transmitted or saved with the information to offer a method of automated checking for any subsequent corruption.” (n.d.b).
Collision
- The CSRC explains that within the context of hash features, collision is when “two or extra distinct inputs produce the identical output” (n.d.b).
Collision resistance property
- The CSRC states that collision resistance property is “an anticipated property of a cryptographic hash operate whereby it’s computationally infeasible to discover a collision” (n.d.c).
Determinism property
- Hash features are all the time deterministic in nature, which means the hash worth is “purely decided by its inputs, the place no randomness is concerned within the mannequin” (Techopedia, 2019). Hash features “will all the time provide you with the identical consequence given the identical enter” (Techopedia, 2019).
Digital signature
- In accordance with the Oxford English Dictionary, a digital signature is “an digital signature … one generated and verified by public key encryption” (OED, n.d.c).
Distributed ledger know-how (DLT)
- A ledger is “a record-book; a e-book that lies completely in some place; ordinarily employed for recording mercantile transactions” (OED, n.d.d).
- “DLT-based platforms check with a set of applied sciences and completely different fields of science (like algebra and statistics) that, grouped collectively, allow the storage and change of information in a decentralized and safe method for which no central regulator is required” (Lesmes, 2019, np).
- They “facilitate the storage, processing, and change of information, bringing greater pace and larger transparency and reliability than conventional legacy methods” (Lesmes, 2019, np).
Error-correcting code (ECC)
- Katz and Sprint describe ECCs as “an encoding scheme that transmits messages as binary numbers, in such a approach that the message will be recovered even when some bits are erroneously flipped. They are utilized in virtually all instances of message transmission, particularly in information storage the place ECCs defend towards information corruption” (n.d.).
Hash or hashing
- “Hashing is a time period that refers to using an algorithm – known as a hash operate – to transform a bit of info into an alphanumeric string of characters like this: e9ffc424b79f4f6ab42d11c81156d3a17228d6b1edf4139be78e948a9332d7d8. Hashing is a generally used method in laptop science and cryptography” (City and Pineda, 2018, p. 16).
- “The manipulation of log recordsdata can take many various expressions, however the prospects to acknowledge such manipulations additionally differ drastically. ‘File verification’ mechanisms search to make sure {that a} file has not been modified. For instance, checksum or hash strategies can be used to confirm content material, authors or digital possession” (Radinger-Peer and Kolm, 2020, p. 134).
- In computing, hashing is “the project of a numeric or alphanumeric string to a bit of information through the utility of a operate whose output values are all the identical variety of bits in size” (OED, n.d.e).
Key era
- The method of key era can be accomplished “both as a single course of utilizing a random bit generator and an accepted algorithm, or as created throughout key settlement or key derivation” (CSRC, n.d.d).
Message integrity
- Message integrity refers to “the validity of a transmitted message. Message integrity signifies that a message has not been tampered with or altered” (PCmag Encyclopedia, n.d.).
Message digest
- Message digest will be understood as “the fixed-length bit string produced by a hash operate,” in line with the CSRC (n.d.e). Synonyms of this time period are “digital fingerprint, hash output, or hash worth” (CSRC, n.d.e).
Node
- The CSRC defines a node as “an particular person system inside the blockchain community” (n.d.f).
Non-fungible token (NFT)
- In accordance with Merriam-Webster, NFTs are “a novel digital identifier that can’t be copied, substituted, or subdivided, that’s recorded in a blockchain, and that’s used to certify authenticity and possession (as of a particular digital asset and particular rights regarding it)” (n.d.).
Pre-image
- The CSRC defines a pre-image as “a message X that produces a given message digest when it’s processed by a hash operate” (n.d.g).
Pre-image resistance
- This property of hash features is outlined by the CSRC as being “an anticipated property of a cryptographic hash operate such that, given a randomly chosen message digest, message_digest, it is computationally infeasible to discover a preimage of the message_digest” (n.d.h). Please see message digest and pre-image if additional clarification is important.
Proof of work (PoW)
- Chowdhury explains that “PoW is an financial measure to discourage denial-of-service assaults and different service abuses akin to spam on a community by requiring some work from the service requester, normally which means processing time by a pc” (2019, p. 56).
Proof of stake (PoS)
- Chowdhury explains PoS by evaluating it with PoW, saying, “as an alternative of constructing operations costly by consuming electrical energy, this technique requires miners to deposit a wealth that dangerous actors will lose if [they] attempt to bend the foundations” (2019, p. 19).
Provenance
- In accordance with the Oxford English Dictionary, provenance is “the very fact of coming from some explicit supply or quarter; origin, derivation,” and in relation to the notion established by the humanities area, “the historical past of the possession of a murals or an vintage, used as a information to authenticity or high quality; a documented report of this.” (n.d.f)
- “Knowledge provenance tracks the origin of data with the aim of bettering belief amongst events. Knowledge provenance is a crucial requirement for a spread of purposes akin to meals security, provide chains, and monitoring of epidemic outbreaks. Many of those purposes are inherently distributed and require excessive ranges of privateness and belief” (Lautert, Pigatto, and Gomes 2020, p. 1).
- “Provenance is the method or strategies utilized to trace the origin, authorship and historical past of any given object. It was initially used within the context of artworks to make it possible for an object was created by the claimed creator” (Lautert, Pigatto, and Gomes 2020, p. 1).
Public key
- The Oxford English Dictionary defines a public key as “a cryptographic key that may be obtained and utilized by anybody to encrypt messages in such a approach that the encrypted messages will be deciphered solely by utilizing a second ‘non-public’ key recognized solely to the recipient.” (n.d.g).
Public key infrastructure
- The CSRC explains that public key infrastructure is “the structure, group, strategies, practices, and procedures that collectively assist the implementation and operation of a certificate-based public key cryptographic system. Framework established to challenge, preserve, and revoke public key certificates” (n.d.i).
Weak collision resistance
- Hirose defines weak collision resistance as “the likelihood of failure to discover a collision is just not negligible” (2004, p. 88).
Appendix B: Strategies
Key phrases
- Authentication
- Certification
- Verification
- Utilized
- Distributed ledger know-how
- DLT
- Cryptography
- Knowledge
- Authorities
- Blockchain
- Cryptographic key
- Hash operate
- Digital signature
- Knowledge circulate
- Software
- Checksum
- Knowledge provenance
- Digital fingerprint
- Knowledge safety
- Distinctive identifiers
- Error-correcting codes
Searches
- (“Distributed ledger know-how”) OR (DLT)
- (“Blockchain”) AND (“Authent*) OR (Certif*) OR (Verif*)
- (“Digital signature”)
- (“Hash operate”) AND (“Cryptography”)
- (“Authorities”) AND (“Utilized”) AND (“Cryptographic key”)
- (“Authorities”) AND (“Utilized”) AND (“Distributed ledger know-how”) OR (“DLT”)
- (“Authorities”) AND (“Utilized”) AND (“Digital fingerprint”)
- (“Error-correcting codes”) AND (“Utilized”) NOT (“Algebra”)
- (“Error-correcting codes”) AND (“Utilized”) AND (“Authorities”)
- (“Checksum”) AND (“Verif*) AND (“Utilized”)
- (“Knowledge provenance”) AND (“Blockchain”)
- (“Knowledge circulate”) AND (“Knowledge provenance”)
- (“Digital signature”) OR (“Digital fingerprint”) AND (“Knowledge safety”)
- (“Distinctive identifiers”) AND (“Knowledge safety”)
- (“Error-correcting codes”)
References
Al-Kuwari, S., Davenport, J. H., and Bradford, R. J. (2011). Cryptographic Hash Capabilities: Latest Design Developments and Safety Notions. Brief Paper Proceedings of Inscrypt ’10, 1–37. Retrieved 2022, from https://eprint.iacr.org/2011/565.pdf.
Aljeaid, D., Ma, X., and Langensiepen, C. (2014). Biometric identity-based cryptography for e-Authorities surroundings. Proceedings of 2014 Science and Info Convention, SAI 2014. 581-588. https://doi.org/10.1109/SAI.2014.6918245.
Batista, D., Kim, H., Lemieux, V. L., Stancic, H., and Unnithan, C. (2021). Block and provenance: How a technical system for tracing origins, possession and authenticity can remodel social belief. In V. Lemieux and C. Feng (eds.) Constructing decentralized belief: Multidisciplinary views on the design of blockchains and distributed ledgers (First ed., pp. 111–128). Springer. https://doi.org/10.1007/978-3-030-54414-0.
Bell, M., Inexperienced, A., Sheridan, J., Collomosse, J., Cooper, D., Bui, T., Thereaux, O., & Higgins, J. (2019). Underscoring archival authenticity with blockchain know-how. Insights: The UKSG Journal, 32. https://hyperlink.gale.com/apps/doc/A594619025/AONE?u=anon~eafb9693&sid=googleScholar&xid=e1544e71
Canada’s Public Coverage Discussion board. (2014). Northern Connections: Broadband and Canada’s Digital Divide. Public Coverage Discussion board: Reviews. Retrieved January 27, 2022, from https://ucarecdn.com/68b98fff-32c9-4904-904c-09b1d98cdd2e/
Chandler, S. (2021, December 22). Proof of stake vs. proof of labor: Key variations between these strategies of verifying cryptocurrency transactions. Enterprise Insider. https://www.businessinsider.com/personal-finance/proof-of-stake-vs-proof-of-work
Chowdhury, N. (2019). Inside blockchain, Bitcoin, and cryptocurrencies. Auerbach.
Communications Safety Institution Canada. (2021, December 6). Ministers urge Canadian organizations to take motion towards Ransomware. Canada.ca. Retrieved January 26, 2022, https://www.canada.ca/en/communications-security/information/2021/12/ministers-urge-canadian-organizations-to-take-action-against-ransomware.html
Pc Safety Useful resource Middle. (n.d.a). Certification authority. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/certification_authority
Pc Safety Useful resource Middle. (n.d.b). Collision. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/collision
Pc Safety Useful resource Middle. (n.d.c). Collision resistance. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/collision_resistance
Pc Safety Useful resource Middle. (n.d.d). Key era. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/key_generation
Pc Safety Useful resource Middle. (n.d.e). Message digest. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/message_digest
Pc Safety Useful resource Middle. (n.d.f). Node. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/node
Pc Safety Useful resource Middle. (n.d.g). Preimage. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/preimage
Pc Safety Useful resource Middle. (n.d.h). Preimage resistance. In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/preimage_resistance
Pc Safety Useful resource Middle. (n.d.i). Public key infrastructure (PKI). In Pc Safety Useful resource Middle: Glossary. Retrieved from, https://csrc.nist.gov/glossary/time period/public_key_infrastructure.
De Filippi, P. D. F. (2018). Blockchain and the legislation: The rule of code. Harvard College Press. https://doi.org/10.4159/9780674985933
Hirose, S. (2004). Yet one more definition of weak collision resistance and its evaluation. In Lim JI., Lee DH. (eds) Info Safety and Cryptology - ICISC 2003. ICISC 2003. Lecture Notes in Pc Science, vol. 2971. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-24691-6_8
Huang, J., O’Neill, C., and Tabuchi, H. (2021, September 3). Bitcoin makes use of extra electrical energy than many nations. How is that doable? The New York Occasions. https://www.nytimes.com/interactive/2021/09/03/local weather/bitcoin-carbon-footprint-electricity.html
Industrial Analysis Help Program. (2019). Blockchain publishing prototype. Nationwide Analysis Council of Canada. Authorities of Canada. https://nrc-cnrc.explorecatena.com/en
Ipsos Public Affairs for Canada’s Centre for Worldwide Governance Innovation. (2019). World Survey Web Safety & Belief. CIGI-Ipsos World Survey Web Safety Belief Half I & II: Web safety, on-line privateness & belief. Retrieved from, https://www.cigionline.org/websites/default/recordsdata/paperwork/2019percent20CIGI-Ipsospercent20Globalpercent20Surveypercent20-%20Partpercent201percent20percent26percent202percent20Internetpercent20Securitypercent2Cpercent20Onlinepercent20Privacypercent20percent26percent20Trust.pdf
Jiang, S. (2021, November 9). Discord’s hints about crypto, NFTs are tearing its neighborhood aside. Kotaku. https://kotaku.com/discords-hints-about-crypto-nfts-are-tearing-its-commu-1848023955
Katz, A., & Sprint, S. (n.d.). Error correcting codes. Good Math & Science Wiki. Retrieved January 27, 2022, from https://good.org/wiki/error-correcting-codes/
Kickstarter. (2022). Let’s construct what’s subsequent for crowdfunding inventive initiatives. Kickstarter. https://www.kickstarter.com/articles/lets-build-whats-next-for-crowdfunding-creative-projects?ref=section-homepage-promo-the-future-of-crowdfunding-creative-projects
Lacity, M. (2018). A supervisor’s information to blockchains for enterprise: From realizing what to realizing how. SB Publishing.
Lautert, F., Pigatto, D. F., and Gomes, L. (2020). A fog structure for privacy-preserving information provenance utilizing blockchains. Proceedings of the 2020 IEEE Symposium on Computer systems and Communications (ISCC). https://doi.org/10.1109/ISCC50000.2020.9219724
Lemieux, V. (2016a). Trusting information: Is Blockchain know-how the reply? Information Administration Journal, 26(2), 110–139. https://doi.org/10.1108/RMJ-12-2015-0042
Lemieux, V. (2016b). Blockchain for recordkeeping: Assist or hype? SSHRC Technical Report, p. 1–31.
Lemieux, V. (2019). Blockchain and public report retaining: Of temples, prisons, and the (re) configuration of energy. Frontiers Blockchain, 2, n.p. https://doi.org/10.3389/fbloc.2019.00005
Lesmes, J. (2019). The web of worth: How distributed ledger applied sciences will reshape the monetary companies business (First ed.). O’Reilly Media.
Maull, R., Godsiff, P., Mulligan, C., Brown, A., & Kewell, B. (2017). Distributed ledger know-how: Functions and implications. Strategic Change, 26(5), 481–489. https://doi.org/10.1002/jsc.2148
Merriam-Webster. (n.d.). Non-fungible token. In Merriam-Webster.com dictionary. Retrieved January 26, 2022, from https://www.merriam-webster.com/dictionary/non-fungiblepercent20token
Mohamed, Ok. S. (2020). New frontiers in cryptography: Quantum, blockchain, light-weight, chaotic and DNA (1st ed.). Springer. https://doi.org/10.1007/978-3-030-58996-7
Morse, J. (2021, December 16). Kickstarter stated it’s transferring to the blockchain, and creators are pissed: Decentralized frustration. Mashable. https://mashable.com/article/kickstarter-protocol-blockchain-creator-reaction
Nationwide Institute of Requirements and Expertise. (2015, August 5). NIST releases SHA-3 Cryptographic Hash Customary. NIST: Information. Retrieved January 27, 2022, from https://www.nist.gov/news-events/information/2015/08/nist-releases-sha-3-cryptographic-hash-standard
Nationwide Analysis Council Canada. (2018). Exploring blockchain for higher enterprise. Authorities of Canada. https://nrc.canada.ca/en/tales/exploring-blockchain-better-business
Ølnes, S., Ubacht, J., & Janssen, M. (2017). Blockchain in authorities: Advantages and implications of distributed ledger know-how for info sharing. Authorities Info Quarterly, 34(3), 355–364. https://doi.org/10.1016/j.giq.2017.09.007
Oxford English Dictionary. (n.d.a). Blockchain. In Oxford English Dictionary. Retrieved from https://www-oed-com.proxy.library.carleton.ca
Oxford English Dictionary. (n.d.b). Checksum. In Oxford English Dictionary. Retrieved from https://www-oed-com.proxy.library.carleton.ca
Oxford English Dictionary. (n.d.c). Digital Signature. In Oxford English Dictionary. Retrieved from https://www-oed-com.proxy.library.carleton.ca
Oxford English Dictionary. (n.d.d). Distributed Ledger Expertise. In Oxford English Dictionary. Retrieved from https://www-oed-com.proxy.library.carleton.ca
Oxford English Dictionary. (n.d.e). Hashing. In Oxford English Dictionary. Retrieved from https://www-oed-com.proxy.library.carleton.ca
Oxford English Dictionary. (n.d.f). Provenance. In Oxford English Dictionary. Retrieved from https://www-oed-com.proxy.library.carleton.ca
Oxford English Dictionary. (n.d.g). Public Key. In Oxford English Dictionary. Retrieved from https://www-oed-com.proxy.library.carleton.ca
PCmag Encyclopedia. (n.d.). Message Integrity. PCmag. Retrieved January 27, 2022, from https://www.pcmag.com/encyclopedia/time period/message-integrity#:~:textual content=Messagepercent20integritypercent20meanspercent20thatpercent20a,beenpercent20tamperedpercent20withpercent20orpercent20altered.& textual content=Integritypercent20checkingpercent20ispercent20onepercent20component, Parkerianpercent20Hexadpercent20andpercent20datapercent20integrity.
Pearson, J. (2021, November 11). Discord backs off of crypto after whole web yells at CEO. Vice. https://www.vice.com/en/article/7kb9dg/discord-backs-off-of-crypto-after-entire-internet-yells-at-ceo
Plunkett, L. (2021, December 17). Kickstarter broadcasts blockchain future, doubles down after customers say “no thanks.” Kotaku. https://kotaku.com/kickstarter-announces-blockchain-future-doubles-down-a-1848231993
Prathibha, Sona, T. R., & Krishna Priya, J. (2021). Secured Storage and Verification of Paperwork Utilizing Blockchain Expertise. In Remodeling Cybersecurity Options utilizing Blockchain (pp. 71–90). Springer Singapore. https://doi.org/10.1007/978-981-33-6858-3_5
Radinger-Peer, W. and Kolm, B. (2020). A blockchain-driven method to satisfy the GDPR recording necessities. In Treiblmaier, H. and Clohessy, T. (Eds.), Blockchain and distributed ledger know-how use instances: Functions and classes discovered (pp. 133-148). Springer. https://doi.org/10.1007/978-3-030-44337-5
Ruoti, S., Kaiser, B., Yerukhimovich, A., Clark, J., and Cunningham, R. (2020). Blockchain Expertise: What’s it good for? Communications of the ACM, 63(1), 46–53. https://doi.org/10.1145/3369752
Solana. (2021, November 24). Solana’s vitality use report: November 2021. Solana. https://solana.com/information/solana-energy-usage-report-november-2021
Statistics Act, Revised Statutes of Canada (1985, c. S-19). Retrieved from the Justice Legal guidelines web site: https://legal guidelines.justice.gc.ca/eng/acts/S-19/
Statistics Canada. (2018, October 5). Acts and rules. Statistics Canada. Retrieved January 26, 2022, from https://www.statcan.gc.ca/en/about/frp/frp?MM=as
Statistics Canada. (2021). Departmental Outcomes Report (Catalogue no. 11-628-X). Retrieved from, https://www.statcan.gc.ca/en/about/drr/2020-2021/index
Techopedia. (2019, August 29). What’s deterministic algorithm?—definition from Techopedia. Techopedia.com. Retrieved January 28, 2022, from https://www.techopedia.com/definition/18830/deterministic-algorithm
Treiblmaier, H. (2018). The affect of the blockchain on the availability chain: A theory-based analysis framework and a name for motion. Provide Chain Administration, 23(6), 545–559. https://doi.org/10.1108/SCM-01-2018-0029
Treiblmaier, H., & Clohessy, T. (2020). Preface. In H. Treiblmaier and T. Clohessy (eds.), Blockchain and distributed ledger know-how use instances: Functions and classes discovered (1st ed., pp. v-vii). Springer Worldwide Publishing. https://doi.org/10.1007/978-3-030-44337-5
City, M. C. and Pineda, D. (2018). Contained in the black blocks: A policymaker’s introduction to blockchain, distributed ledger know-how and the “web of worth.” Mowat Centre for Coverage Innovation, College of Toronto.
Welfare, A. (2019). Commercializing blockchain: Strategic purposes in the actual world. Wiley.
Xiao, Y. and Watson, M. (2019). Steerage on conducting a scientific literature evaluate. Journal of Planning Schooling and Analysis, 39(1), 93–112. https://doi.org/10.1177/0739456X17723971
Zheng, X., Zhu, Y., & Si, X. (2019). A survey on challenges and progresses in blockchain applied sciences: A efficiency and safety perspective. Utilized Sciences, 9(22), 1–24. https://doi.org/10.3390/app9224731